Everyone's sensitive data in the cloud is at risk! Quantum computers will have the processing power to break the classical encryption codes that now secure your files, healthcare and financial records, your corporate or personal confidential documents.
100% Free for Non-Commercial Use*
A process on the client-side that begins by applying AES 256-bit encryption to the user’s original data set and then performing All-or-Nothing transform. Finally, Private.me’s proprietary Information Dispersal Algorithm (IDA) is applied to the output to produce multiple slices of random data sets that is effectively hack-proof or “theoretically secure”.
Our Information Dispersal Algorithm (IDA) is the next-generation cryptosystem that is “theoretically secured” and extremely efficient. The output IDA data sets are indistinguishable from random data sets and therefore mathematically impossible to penetrate. Your data is fully protected when the three data sets are in transit separately and when they are at rest stored separately at three remote locations. Our IDA process is transparent and can be audited by third parties at any time.
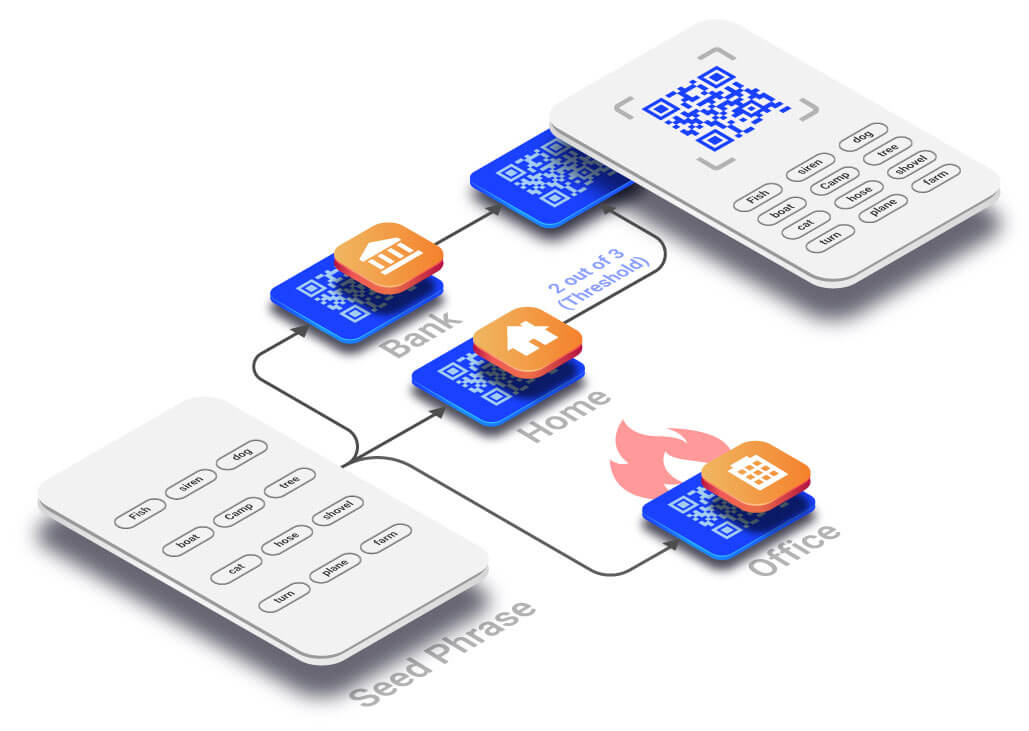
In the event that a sliced data set is unavailable for retrieval or it has retrieved a corrupt payload, the original data remains safe. In order to re-create the original data set, a minimum threshold (2 out of 3 slices) is required to be reassembled to re-create the original data set. To protect each data set, the platform leverages Kerberos based authentication system in four “realms” or independent authentication authorities - Private.me central server plus the three storage nodes. To ensure none of the four services can retrieve a threshold of slices, a series of sophisticated cryptographic safeguards are kept in place. Please ask for our whitepaper for more information.
Our technology is ideal for scenarios wherein an organization has cloud storage needs but prefers not to extend full trust to a third-party remote data storage provider for safekeeping and access control enforcement. Our algorithm provides assurance against even a server system administrator compromising the data. This user protection extends to three areas: denial of legitimate access, tampering, and unauthorized decryption.
Building a cloud document or data storage product with the Private.me platform solves the problem of trust of remote servers, specifically by removing the need for blind trust. Private.me uses a secure in-depth, layered approach involving not only end-to-end data encryption but also cryptographic data dispersal adding significant security assurance to cloud storage. The system works by encrypting and securely slicing data on the client-side, then uploading the slices to separate cloud servers. Successful retrieval and decryption later require access to multiple servers to retrieve slices for decryption. Without the successful threshold, the data is immune even to brute force attempts to compromise it.

With email and other common messaging technologies are widely known to be subject to potential vulnerabilities, businesses need alternative channels to encourage best practices and safeguard restricted and sensitive information. With disparate systems, this is a difficult or impossible task to accomplish securely. However, a communication tool built on the Private.me platform uses the strong guarantees of end-to-end encryption and rigorous user authentication to safeguard data in transit. Even the intermediate cloud application hosts involved in transmitting messages are unable to decrypt a message - only intended recipients have access.

Key storage and management reflect a special case of the Private.me cloud approach that benefits from the secure data dispersal technique. By cryptographically splitting mission-critical keys for dispersal across multiple hosts, an organization can benefit from the same kind of distinct assurances used in the most critical national defense contexts, such as missile silo key protocols. In this case, the secret cryptographic keys are protected even in the event of a compromise of one of the storage servers due to the strong cryptographic slicing algorithm. Gaining access to only one slice does nothing for an attacker - a valid threshold is required to decrypt the key.

Documents and data stored in either workstations or servers on-premises are at risk from ransomware, which can spread rapidly through an organization and effectively destroy critical data. Documents and data stored in the Private.me cloud are insulated from any on-premises attacks. In addition, the use of the Private.me cloud's key escrow service protects in the event of a total loss of client-side data, which could otherwise be a loss due to end-to-end encryption.
Secure your cloud service for your customers! Build on our hackproof backend storage and cummunication platform. Our API makes it easy to preconnect to your existing application.
Secure your cloud service for your customers! Build on our hackproof backend storage and communication platform. Our API makes it easy to connect to your existing application.
Deploy it on your private cloud infrastructure with complete autonomy. This solution is ideal for Storing highly classified data.
A hybrid model by combining your private cloud infrastructure with a public cloud provider such as Amazon AWS. It achieves the same level of security as private cloud deployment but can be more economical upfront.
Build on our hackproof backend storage and communication platform. Our API makes it easy to connect your existing application to working with all top storage providers.

Xecret.io uses Private.me XOR-based Information Dispersal Algorithm (XOR-IDA) to create a set of cryptographic QR codes. These QR codes store confidential data such as crypto wallet seed phrases, private keys, or any critical passwords. This unique approach to offline storage is the only solution to simultaneously protect against loss, fire, and theft.